- 8
Speakers - 8
Security Topics - 100 yrs
Combined Experience
Helping Survivors
We believe everyone deserves to be safe, and also to feel safe.
- dvTsascw23D
- July 10, 2019
How We Support Our Clients
We work with the client and their support system Protect […]
- dvTsascw23D
- July 10, 2019
A Message From Our Director
I’ve had the privilege of working with Operation Safe Escape […]
Our Speakers
Shannon Miller
Shannon Miller
Privacy Fundamentals: Precautions and PracticesWe all have someone or something we want to protect. Understanding your threat model, the basics of secure communication, and how to protect your privacy and digital devices is essential to staying safe. This talk focuses on assessing risk, account security and understanding your digital footprint.
Privacy Advocate & Investigator at LockDownYourLife.com
Julie Beck
Julie Beck
Survivor to Hunter: An Overcomer’s Story of Surviving Domestic Violence and Cult ControlTopic Title: Survivor to Hunter: An Overcomer’s Story of Surviving Domestic Violence and Cult Control
Julie has over 18 years experience in technology and cyber security. She is certified as an ethical hacker and in OSINT. As a survivor of domestic violence and abuse, she now dedicates her time to giving back to organizations like Operation Safe Escape and Skull Games. She leads the OSINT Team at OSE.
- Email drbeck7997@gmail.com
Katelyn Bowden
Katelyn Bowden
Why Your Privacy Matters (and How to Take it Back)Katelyn Bowden is a hacker, an activist, and a community manager. She is a member of the famed hacker collective, the Cult of the Dead Cow (cDc) since 2020. She previously was the founder and CEO of BADASS, a nonprofit dedicated to eradicating revenge porn. Currently, Katelyn is the CMO and Cofounder of the Veilid Project, as well as a board member for the Veilid Foundation- a nonprofit dedicated to developing apps with privacy built in, on the Veilid network. In her spare time, Katelyn creates cursed artwork and nightmare sculptures.
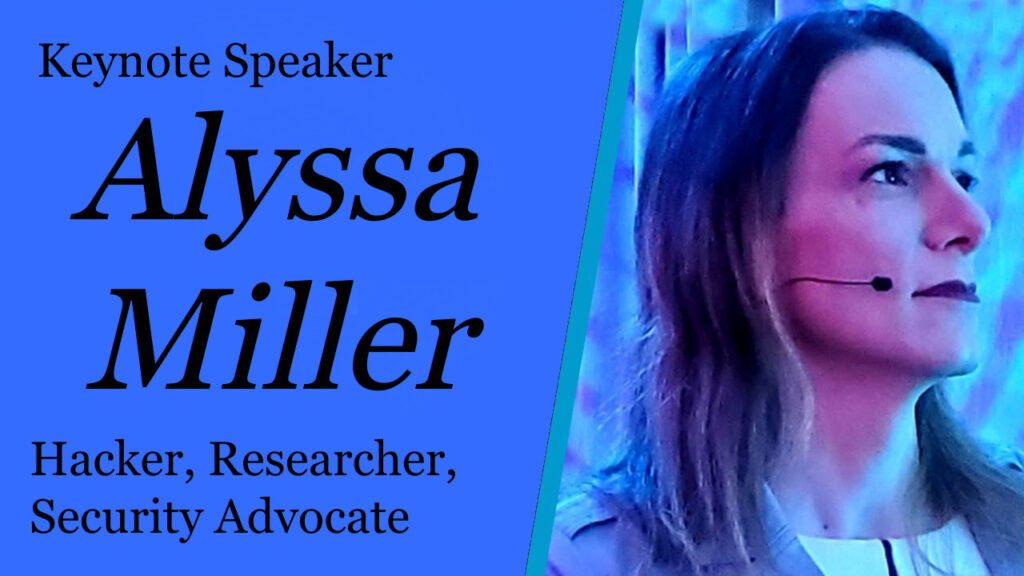
Alyssa Miller
Alyssa Miller
Keynote
From Hobby to Career
From a young age, she has enjoyed exploring and deconstructing technology to learn more about how it works. At 12 years-old, she bought her first computer. From that $1,000 purchase, she launched a hobby that would later become her career. Just seven years later, she was hired to her first full-time salary job as a programmer.
As her career solidified, her natural curiosity continued to drive her development. After serving as a lead programmer for years, she transitioned to a penetration testing role. It wasn’t long before she took on leadership of the team, and oversaw vulnerability management for the entire organization. Since that time, she’s continued to develop both her technical and business skills. As a consultant, she has worked closely with business leaders to build enterprise security programs. To this day, she continues to focus on developing strategies for securing technology systems, devices, and applications.
Alyssa Miller is a hacker, security researcher, advocate, and international public speaker with over 15 years of experience in cyber security. She believes that in today’s inter-connected world, protecting privacy and building trust with secure systems are critical to protecting our way of life. As a result, she discusses real-world issues that that affect people both within and outside the security community.
From Hobby to Career
From a young age, she has enjoyed exploring and deconstructing technology to learn more about how it works. At 12 years-old, she bought her first computer. From that $1,000 purchase, she launched a hobby that would later become her career. Just seven years later, she was hired to her first full-time salary job as a programmer.
As her career solidified, her natural curiosity continued to drive her development. After serving as a lead programmer for years, she transitioned to a penetration testing role. It wasn’t long before she took on leadership of the team, and oversaw vulnerability management for the entire organization. Since that time, she’s continued to develop both her technical and business skills. As a consultant, she has worked closely with business leaders to build enterprise security programs. To this day, she continues to focus on developing strategies for securing technology systems, devices, and applications.
Bryson Bort
Bryson Bort
Security Choose your own AdventureIn the vein of old school Choose Your Own Adventures, this is a custom created story that leads the audience through an incident response including technical and business considerations. The audience votes through a live poll on decision points in the story including detection, identification, response, remediation, and threat hunting for like compromises. Communication with the appropriate stakeholders and your team is key throughout the phases. The core "story" will be the majority of the session, but will generate significant discussion and Q&A. After the talk, we will release a free tool that will allow the audience to continue to play and learn on their own through the different decision points.
"I created this exercise (and corresponding tool) as a new way to engage an audience to teach Blue Team concepts in process, organizational considerations, and technical techniques beyond the standard Powerpoint lecture. It has been play-tested with over 1000 players and found that it works well from beginner to expert level in facilitating discussion and insights."
Will Baggett
Will Baggett
Broken Arrow: Detangling Domestic Disputes DigitallyI will present the playbook used to assist domestic abuse victims in detangling their domestic abuser from their digital footprint. This talk is the core of our intake process at OSE, where I provide a methodology to identify the most common methods of domestic stalking that a non-technical person can use to assist a survivor.
I cover cellular, social media, financial, and fiscal areas where most attackers can be mitigated as well as proper documentation steps to assist the end user.
Will Baggett is the director of digital forensics at operation safe escape and draws from his experience as a former CIA officer specializing in Technical and HUMINT Operations and NATO SOF Cyber Security SME to apply the counterintelligence mindset. The same Insider Risk and Fraud Awareness methodology can be applied to the domestic situation-what data can be gathered by the victim, what technical threats could be used against a person in their own house and how to detect the threat.
Edna Jonsson
Edna Jonsson
Revenge Porn and Deep Fake Image Shakedowns
Edna Jonsson, CySA+, SSCP, is a cybersecurity analyst and engineer. A current cybersecurity and information assurance master’s degree student at online Western Governors University, Edna is past president of the WGU Cyber Club and participant in the National Cyber League and National Collegiate Cyber Defense Competitions. Co-author of the Infosec Survival Guide: SECOND EDITION, Edna has been an active member of the local cybersecurity community and runs the Career Village at BSides Orlando.
Ruddy Wang
Ruddy Wang
Cell Phone Security and SafetyFor most of us, our lives are kept on our mobile devices. We keep pictures there. Our schedules. Our communication. Even our finances. For anyone, the impact of a data breach or security incident is immeasurable, but for survivors of abuse it can be a matter of life and death. Ruddy Wang shares techniques for securing mobile devices even when the abuser has access to them.
Ruddy is Head of Growth at Cape, a privacy-first mobile carrier, and has lead growth, operations, and policy at technology companies across multiple sectors. At Uber, he launched over 100 cities in Brazil and led new business expansion in Latin America, and at Facebook he managed public policy in APAC and Latin America. At both Uber and Facebook, he worked with civil society organizations to launch programs regarding gender-based violence and harassment. Prior to tech, Ruddy was a US diplomat with experience in Africa, Latin America, and Asia.
Samantha Gamble
Samantha Gamble
Targeting and Disrupting Online Child Exploitation Groupssajolida
sajolida
How to use Tails, The Amnesic Incognito Live System, for secure communicationsTails, "The Amnesiac Incognito Live System," is a computer operating system designed to protect the user. Because it usually boots from a USB drive, it bypasses the computer's hard drive and doesn't leave a trace of what's been done. This can allow a survivor to communicate with their support system or search for resources without leaving signs on a shared computer. This talk will show how to configure and use Tails safely.
Sajolida is a UX Designer at Tor Project who has been working on making Tails useful and easy to use since 2011. He has a wide range of technical and non-technical skills that allow him to communicate with designers, software developers, and users alike.
Chris Cox
Chris Cox
HostChris Cox is the Director of Operation Safe Escape, founder and past president of the Operations Security Professional's Association, and general security nerd. In addition to his work with OSE, past professional roles include CIO of the U.S. Army National Training Center, Cybersecurity Instructor for the DoD, OPSEC Analyst for the Department of Energy, and multiple other infosec roles.
ProtectCon 2025
"Promoting rights and outcomes through technology, engagement, collaboration, and transformation." ProtectCon 2025 is the third iteration of the Operation Safe Escape conference series, which invites experts in safety, security, and tech to share their experience and knowledge with those on the front line of combating domestic violence, stalking, and trafficking. Our mision is to improve the security posture for allies, advocates, and survivors and improve outcomes for all. We believe everyone deserves to be safe AND to feel safe, and we'll work every day to help make that a reality.
Expert Speakers
The speakers are all experts in their respective fields, most with decades of relevant experience to share
Connecting People
Building opportunities to connect with peers and allies to share information and resources















